Get Advanced Insights on Any Topic
Discover Trends 12+ Months Before Everyone Else
How We Find Trends Before They Take Off
Exploding Topics’ advanced algorithm monitors millions of unstructured data points to spot trends early on.
Keyword Research
Performance Tracking
Competitor Intelligence
Fix Your Site’s SEO Issues in 30 Seconds
Find technical issues blocking search visibility. Get prioritized, actionable fixes in seconds.
Powered by data from
20 Biggest Crypto Heists To Date (2023)
Crypto heists are big businesses for hackers these days.
The concept of a decentralized financial system - where every transaction is recorded and traceable - seems like it would be hacker-proof. However, poor system oversight and limited vetting in 3rd party services have left some networks extremely vulnerable.
For example, in 2021, 76% of crypto heists were run by external hackers who found a way to use flash loan exploits. Over $14 billion in cryptocurrency was stolen from DeFi ecosystems last year. And the exploits continue: in the first quarter of 2022 $1.2 Billion worth of crypto was stolen by hackers.
With that, here are the biggest crypto heists to date (by total dollar amount stolen):
20. Linode - $228 Thousand
Year: 2012
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 46.6K BTC
Recovered? No
Background:
Cloud hosting provider Linode provides Linux-powered virtual machines for various applications. The company also offers a cloud server for decentralized apps (dApps) to deploy fast, efficient, native SSD cloud servers.
In 2012, an overnight heist occurred when a vulnerability in the customer support system was used to obtain administrator access to the servers and then conduct an unauthorized transfer of BTC from the hot wallets. A few heavy hitters in the crypto industry - including Gavin Andreson, Bitcoin’s lead programmer, and Marek Palatinus, CEO of Satoshi Labs - were directly impacted by the theft. These industry heavyweights personally lost 46.6K Bitcoin (BTC) in the crypto heist.
If this hack happened in 2022, the loss would have been worth $1.8 Billion. It’s the biggest crypto-related heist of Linode servers yet, but it’s not its only instance or the most significant loss due to their server negligence. From 2012 to 2015, Linode experienced at least five major server hacks, with the largest heist totaling over $250 M in losses in 2013.
19. Bitcoinica - $460 Thousand
Year: 2012
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 43K BTC
Recovered? No
Background:
Originally dubbed the “Bitcoin trading platform for everyone,” Bitcoinica burst onto the crypto scene in 2011 with lots of promise. Bitcoinica aimed to offer services for traditional market trading like margin trading, short selling, stop-loss orders, and guaranteed liquidity. Since the cryptocurrency market was still very young, it was the first significant player to offer these sorts of advanced trading features.
Just one year after it made its global debut, in March of 2012, a security lapse on the Linode cloud servers where the application was stored made it possible for hackers to gain unauthorized access. Bitcoinica’s Bitcoin wallets were depleted by the end of the night, prompting the company to shut down temporarily. The company reopened a few days later, only to be subjected to a second heist in May of the same year and then the third one in July. After suffering three separate heists in just four months, Bitcoinica closed its doors for good in November 2012.
The crypto heists that impacted Bitcoinica were all officially attributed to a 3rd party breach. Since then, speculation has been kept alive on social media around founder Zhou Tong. Crypto enthusiasts believe that his negligence made the company vulnerable, or that the crypto heists could have been an inside job. However, no actions have taken place to investigate Tong formally, and the funds were never fully recovered. If this hack happened in 2022, the loss would have been worth over $2 Billion.
18. Allinvain - $500 Thousand
Year: 2012
Type of Heist: Hacker attack on user’s personal computer
What Was Stolen: 25K BTC
Recovered? No
Background:
Bitcoin enthusiast allinvain was an early cryptocurrency investor and miner, and he used a personal Windows computer to mine and store his Bitcoin tokens - initially worth pennies.
Today, mining is a costly and power-consuming activity. But in the early days of crypto, mining was a little-known hobby that crypto enthusiasts like allinvain did in their spare time. allinvain may have dreamed of becoming one of the earliest and most successful Bitcoin investors and miners. Still, the user became famous for something entirely - becoming the first individual to suffer a significant loss due to a crypto heist.
When the hack happened, allinvain turned to the BitcoinTalk forum to seek help from fellow Bitcoiners. In the post, allinvain explained that the hackers breached their slush’s pool account and stole the password from their personal hard drive. After numerous attempts to restore the wallet or invalidate the thieves’ transfer, all hope was lost.
Followers of the case later speculated that the Bitcoin heist may have been one of the earliest instances of cryptocurrency malware. Whatever the cause, if this hack happened in 2022, allinvain’s loss would have been worth $968 Million.
17. Bitfinex - $72 Million
Year: 2016
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 119K BTC
Recovered? Yes
Background:
The Hong Kong-based Bitcoin exchange Bitfinex is no stranger to criticisms and scandal. When Bitfinex first launched in 2012, it was considered a sort of reborn version of Bitcoinica, which shuttered its doors after one short year. Like Bitcoinica, the peer-to-peer Bitcoin exchange experienced a record-breaking crypto heist. Unlike Bitcoinica, however, Bitfinix was able to survive and grow after one of the most significant hacker exploits in history.
Bitfinex attracts "whale" investors that want to lean into the volatility of Bitcoin. So, when the record-breaking crypto heist hit the company in 2016, it had just rolled out multi-signature wallets - a very appealing feature to its whale clientele.
From 2012 to 2016, single hot wallets were the reason for numerous crypto server exploitations. Multi-signature wallets provide an extra layer of security for customer transactions by dividing up keys amongst several owners. Bitfinex held two private keys, and its authentication partner BitGo held the third. Still, hackers created several layers of false identities and used them to send 2,000 approved transactions to a single wallet from users’ segregated wallets.
The case went cold until February of 2022 when the DOJ traced the stolen crypto back to the wallets of two individuals in New York City. While the DOJ was able to recover all of the stolen crypto funds - worth $3.6 Billion at the time of retrieval - Bitfinex doesn’t plan to return them to its original owners. At the time of the theft, Bitfinex created BFX tokens for impacted customers to redeem, all of which were accepted.
16. EasyFi - $81 Million
Year: 2021
Type of Heist: Inside job (suspected)
What Was Stolen: Private keys to MetaMask admin account, UDS, DAI, USDT, and EASY tokens
Recovered? No
Background:
EasyFi is a DeFi Polygon Network-powered lending protocol founded in 2020.
EasyFi is built on a Layer 2 protocol and managed through a third-party integration like MetaMask that is used alongside a Layer 1 blockchain like Ethereum or Bitcoin. Because Layer 2 protocols rely on intermediaries, they are considered one of the weakest links in the chain. This is partly because the OSI (Open Systems Interconnection) model allows layers in the chain to communicate without establishing a previous connection or familiarity. In a well-planned heist, the attacker exploited the Metamask browser extension by hacking into a computer the CEO used solely for official transfers.
The hacker has not yet been identified, but it’s suspected that the EasyFi crypto heist was an inside job. The hacker seemed to have inside knowledge about which computer to access, that it was infrequently on, and the company only used it at specific times to conduct official transfers. However, shortly after the theft of $81 Million, EasyFi released a plan to compensate all affected parties to restore 100% of the stolen funds. However, to date, the funds have still not been recovered.
15. Liquid - $97 Million
Year: 2021
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: ERC-20 assets and 69 various cryptos
Recovered? No
Background:
Japanese crypto exchange Liquid Global, founded in 2014, is one of the largest cryptocurrency trading platforms in the world. With over $72 Million in daily trading volumes, the company provides major liquidity to the crypto economy.
When a massive exploit of their cross-chain protocol Poly Network went unfixed, exposing the company’s hot wallets, its systems became a playground for one of the biggest crypto heists in history. Through this, the hackers compromised the digital hot wallets on the Liquid server. Over 69 different cryptocurrencies totaling $97 Million were stolen and transferred to four other wallets.
After the hack, rival exchange FTX loaned Liquid $120 Million in debt funding to help settle with new capital generation and liquidity. The stolen funds from the crypto heist have not yet been recovered; however, Liquid has bounced back and was acquired by FTX in February of 2022.
14. CoinBene - $105 Million
Year: 2019
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 109 ERC-20
Recovered? No
Background:
CoinBene entered the market in late 2017. Within one year, it secured a place among the ten largest cryptocurrency exchanges globally, with an average trading volume of over $2.1 Billion. It enjoyed a quick rise to prominence due to its unique ‘transaction fee mining’ model - aka ‘trans-fee mining’. The majority of crypto exchanges charge traders a fee to execute a trade. In trans-fee mining, traders receive a refund of the trade fee through the exchange’s token.
By 2019, many exchanges had developed mechanisms to close the system vulnerabilities, which limited the damage caused by hacks. But later that year, CoinBene underwent routine wallet maintenance over a three-day period that exposed the company to a costly vulnerability to its own wallets that contained tens of millions of dollars of ERC-20 tokens.
Strangely, CoinBene initially denied the hack, but impacted users turned to the Internet to voice their concerns and experiences. It’s unconfirmed if this was an insider job, and the company insists it wasn’t. After the hack, the Etherscan platform discovered that the hacker sent the funds to numerous wallets with company naming conventions - labeled as ‘cold wallet’, ‘marketing’, and ‘team’.
CoinBene has continued to remain silent on the issue. It may not ever be revealed what they discovered from the breach and its suspected coverup.
13. BadgerDAO - $130 Million
Year: 2021
Type of Heist: Hacker malware
What Was Stolen: ~2,100 BTC and 151 ETH
Recovered? Partially; $9M of the original $130M was recovered
Background:
A Decentralized Autonomous Organization (DAO) is an entity run by a computer program that the members of the organization control. This program follows rules that are set down in advance. There is no need for a DAO manager, so this eliminates any bureaucracy or hierarchy issues.
DAOs play an important role in many online communities and organizations. Many focus on fundraising for a cause or purchasing a high-ticket item. Last year, a DAO organized to bid on a copy of the U.S. Constitution! BadgerDAO was created in 2020 for its members to use Bitcoin as collateral across DeFi's various products. One of the BadgerDAO products - Sett Vaults - provided DAO members a way to earn a yield on synthetic assets. Yield farming allows users to lend or borrow crypto on a DeFi platform. In return, lenders can earn cryptocurrency in return for their services.
One year after its formation, BadgerDAO suffered a massive exploit of its Sett Vaults product. The exploit occurred in the user interface, where the hacker used malware to breach dozens of user accounts that were ‘yield farming’ for rewards. Additional permissions are enabled in the vaults through the yield farming interface to allow a 3rd party address to access the funds, which is highly vulnerable to attack.
BadgerDAO did not release the total number of tokens stolen. However, based on traffic analysis, the loss was estimated to be around 2,100 BTC and 151 ETH by the Blockchain data and security analytics company PeckShield. The thieves chased out most of the stolen crypto, leaving only $9 Million to be retrieved and refunded.
12. C.R.E.A.M. Finance - $130 Million
Year: 2021
Type of Heist: Hacker flash loan attack
What Was Stolen: 59 different tokens
Recovered? Partially; $16M of the $130M stolen has been recovered to date
Background:
C.R.E.A.M Finance entered the DeFi lending scene with a flurry of potential in 2020. The DeFi lending protocol aimed to be a leader in financial services for crypto owners to earn a yield on their holdings, much like a savings account.
Most crypto heists to date are due to a system vulnerability that has gone unfixed, allowing the hacker easy access to breach and steal funds from a server. In the case of the C.R.E.A.M. Finance exploit, the hacker used a flash loan attack. By borrowing a lot of funds that don’t require collateral, the hacker then manipulates the asset's price on one platform and sells it quickly on another. This quick breach - sometimes happening in minutes - cost C.R.E.A.M. Finance $130 Million.
C.R.E.A.M Finance is no stranger to hackers finding security issues and vulnerabilities in their network; the company was hacked three times in one year due to flash loan exploits. Since its last exploit, C.R.E.A.M. has struggled to rebound, but it’s still active. It suspended ETH markets at the end of 2021 and did not regain standard functionality.
11. Vulcan Forged - $135 Million
Year: 2021
Type of Heist: Inside job (suspected)
What Was Stolen: 4.5M PYR; private keys to 148 wallets
Recovered? No, but Vulcan forged replaced stolen PYR
Background:
NFTs can be used to sell digital art and music or create unique experiences and in-game items. One promising example of this is Vulcan Forged, a community-based blockchain gaming hub built on Ethereum that develops its own games and supports other 3rd-party game developers.
Because Vulcan Forged is built on Ethereum, it benefits from all the security and stability that the Ethereum blockchain offers. In addition, Vulcan Forged has its own native token, PYR, which powers the ecosystem and rewards users for their contributions.
In late 2021, the NFT gaming platform suffered a massive attack where the hacker accessed private keys to 148 different wallets and subsequently drained them. The Vulcan Forged team quickly identified the issue and took action to mitigate the attack. They contacted exchanges to delist PYR and implemented a hard fork to move the PYR token to a new contract.
The hacker sold all but 2 Million PYR that it stole, which the company was able to recover. Despite the massive loss, Vulcan Forged had enough liquidity to replace the stolen funds in the breached wallets.
10. Bitgrail - $150 Million
Year: 2018
Type of Heist: Inside job (suspected)
What Was Stolen: 17M coins stolen from Nano wallets
Recovered? No
Background:
BitGrail is a digital currency exchange that allows users to buy and sell various cryptocurrencies. Founded in 2014 in Italy, the platform seemed like a popular, emerging platform for digital currency trading. Despite touting its user-friendly interface, a wide variety of supported currencies, and low fees, the platform faced some early criticism.
Many users have alleged that the exchange's software was flawed, leading to frequent losses for traders. Then in early 2018, BitGrail was forced to shut down for several weeks after it was hacked. Hackers were able to gain access to its Nano wallets, resulting in significant losses for many traders on the exchange, with over 17 Million coins stolen.
While BitGrail was able to recover some of the lost funds following the hack, it did not succeed in recovering all of them. The platform eventually filed for bankruptcy and declared that it could no longer operate due to financial difficulties stemming from this incident. Since the 2018 theft, Italian police have opened an investigation into the BitGrail founder, alleging a potential inside job or negligence.
9. Beanstalk - $182 Million
Year: 2022
Type of Heist: 2-fold - Hacker flash loan attack and governance model issue
What Was Stolen: 24.8K ETH and ~100M Bean tokens
Recovered? No
Background:
Beanstalk is a decentralized, credit-based stablecoin protocol - also known as a liquidity pool - built on Ethereum. This particular liquidity pool aims to balance the supply and demand of different cryptocurrency projects. Members of liquidity pools contribute funds to a central funding pool ( “the silo”) to earn rewards when the balanced value of one token (a “bean) nears $1.
DeFi liquidity pools like Beanstalk use a governance protocol that allows members to democratize the voting process to decide how the code evolves. The more tokens one holds, the more percentage of the voting rights one has. In just 13 seconds, the Beanstalk hacker obtained a flash loan for ~$1 Billion in cryptocurrency assets, exchanged it for enough “beans” to gain a 67 percent voting stake in its governance system, and voted to approve a change in the code. This change in the code allowed the transfer of the stolen assets to their wallet and repay the flash loan.
Beanstalk is still technically in business while investigating the crypto heist. It is believed that the company lacked a plan to mitigate any potential breaches. Meanwhile, the attacker is unlikely to be found after moving funds through Tornado Cash, facilitating non-custodial transaction privacy.
8. BitMart - $196 Million
Year: 2021
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 20 different tokens, including BSC-USD, Binance Coin (BNB), BNBPay (BPay), Safemoon, Moonshot, Floki, and BabyDoge
Recovered? No
Background:
It’s not a great sign when security analysis firm Peckshield is the first to notice and report suspicious activity from crypto wallet addresses. But in December of 2021, much to the surprise of cryptocurrency exchange BitMart, Peckshield noticed that around $196 Million was suddenly transferred out of the company’s hot wallets. The hacker seemed well-prepared to breach the system of the then four-year-old company, even naming its Ethereum address “Bitmart Hacker”.
Although BitMart initially denied the claims, it officially reported that the company had suffered a large-scale security breach a few hours later. During the heist, the hacker accessed private keys to the company’s hot wallets and drained them dry. Once the stolen tokens were secure in a new wallet, they were slowly swapped into ETH using a decentralized exchange aggregator. Then, they mixed the stolen tokens with clean ones using Tornado Cash to make them harder to trace.
After the hack, BitMart announced its intent to compensate the customers subjected to the crypto heist entirely. Since BitMart never recovered the stolen funds, the company plans to use funds from its personal reserve to cover the costs of the incident and reimburse affected customers.
7. PancakeBunny - $200 Million
Year: 2021
Type of Heist: Hacker flash loan attack
What Was Stolen: 700K BUNNY tokens and 114k BKB
Recovered? No
Background:
The Binance Smart Chain blockchain (BNB) is a commonly used platform for developing high-performance DeFi apps - aka dApps. When PancakeBunny built its yield optimization protocol on BNB in 2020, its use of smart contracts was heralded as the highest yield option for savvy investors.
The original concept of PancakeBunny was to simplify the yield farming process; yield farming is a common DeFi investment strategy where the user lends or stakes its personal crypto investments in exchange for rewards like compounded interest. The problem is: that when the reward itself is minted, a loophole is created in the system, causing an exploit that hackers can take advantage of if left unaddressed.
In May of 2021, the hacker was able to conduct a flash loan attack, manipulating a code-level process (called a ‘balance’) where the rewards exceeded the expenses. Within seconds, over $200 Million worth of BUNNY tokens and BNB. The money was not recovered. PancakeBunny has been forthcoming about exactly how this crypto heist occurred. Security teams like SlowMist have also published code fixes for other companies to become informed of exactly where it happened and how to fix it to reduce vulnerabilities.
6. KuCoin - $281 Million
Year: 2020
Type of Heist: Hacker exploitation of users’ hot wallets
What Was Stolen: 11.5K ETH, 1K BTC, 19.8M USDT-ETH, 18.5M XRP, 26K LTC, 999K USDT, $147M worth of ERC-20 tokens, $87M worth of Stellar tokens; private keys to hot wallets
Recovered? Partially
Background:
KuCoin became a low-cost alternative exchange for crypto traders when it was released in 2017. With low trading fees, its listings of highly risky and speculative ICOs (Initial Coin Offering), and advanced trading tools and charts, the platform contained robust features for advanced investors.
KuCoin also boasted the industry-standard two-factor authentication for wallets and a higher level of security options for their advanced traders. However, in September of 2020, KuCoin suffered a devastating loss when hackers were able to exploit a vulnerability in its security system. After accessing and draining users’ hot wallets, the thieves swapped the stolen tokens into new types of crypto without going through regulated exchanges.
The hackers behind this $281 Million crypto heist have not yet been apprehended; however, the company recovered 84% of the stolen funds and covered the remainder of the losses itself. The company survived, and after the attack, the company made significant updates to its security system. KuCoin also developed and sponsored a Safeguard Program to share knowledge with their partners about security protocols.
5. Wormhole Bridge - $326 Million
Year: 2022
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 120K ETH
Recovered? Y/N
Background:
Decentralized finance applications (aka dApps) often need to be able to join together with two or more chains to move or share data using blockchain bridges. The protocols, rules, processes, and overall codebases of the joined applications are often very different, making connecting multiple blockchain networks challenging to secure. In the blockchain community, debates about the viability of multi-chain vs. cross-chain vs. single-chain bridges are rampant.
First-generation bridges were not built as a forever solution. And interoperability amongst different platforms with different protocols impedes bridge security. When Wormhole came to market offering nine chain integrations, it became a valued token bridge protocol. Wormhole was intended to be the best of the blockchains, securely connecting multiple blockchain networks for popular dApps like Ethereum and Solana.
In February 2022, developers uploaded a security fix to GitHub ( a code repository) for Wormhole. The hackers exploited the security fix that the developer didn’t yet apply to the prod server. Then, the hacker forged a valid signature for the transaction. Then, collateral assets backing the loan disappeared. Since this landmark crypto heist, the debate surrounding bridges has been invigorated. Although the hackers were not found, Wormhole is offering a $10 Million bounty for the recovery. Meanwhile, Jump Trading - the parent company - restored the value of the $320 Million stolen from users’ wallets.
4. Mt. Gox - $470 Million
Year: 2014
Type of Heist: Hacker exploitation of users’ hot wallets
What Was Stolen: 850K BTC
Recovered? Partially
Background:
The cryptocurrency trading platform Mt. Gox holds a special place in the history of Bitcoin exchanges. During its short-lived history, from 2010 to 2014, over 70% of all Bitcoin transactions took place on its platform. Also, during this time, over 850K Bitcoin tokens were stolen from Mt. Gox.
At the time, trading platforms like Mt. Gox faced limited regulations, and the way that deposit and withdrawal transactions occurred was overly complex and time-consuming. The Mt. Gox platform required users to set up two separate accounts. The platform used one wallet account to store the actual cryptocurrency assets. Mt. Gox used the second account for fiat-based currencies (like USD or GBP). Mt. Gox served as the intermediary to hold the crypto until the transaction or trade was settled.
Unlike all of the biggest crypto hacks, Mt. Gox’s heist was attributed to a ‘slow leak in the system’ that allowed thieves to exploit it repeatedly. After years of an international search, Alexander Vinnik was arrested in Greece and then charged and found guilty of money laundering in connection with the Mt. Gox crypto heist. After a 4-year extradition battle between France, Russia, and the US, he was formally sentenced in October of 2021 to serve a prison sentence in France.
3. Coincheck - $532 Million
Year: 2018
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 500M NEM (XEM)
Recovered? No
Background:
Coincheck is one of the oldest cryptocurrency exchanges, dating back to 2012. The exchange offers crypto transactions and wallet storage services to customers worldwide for numerous types of cryptocurrencies - from NEM to ETH.
In January of 2018, hackers exploited a vulnerability in the security system that gave them access to users’ hot wallets. A hot wallet is a crypto wallet that is connected to a server online. NEM developers actually discovered the breach and started to find and mark the tokens as stolen, but it was too late. BIG Blockchain Intelligence Group claimed to have tracked the proceeds to an exchange in Vancouver, but they were not easily found or apprehended.
Initially, Coincheck vowed to repay customers 88.549 yen for each stolen coin from its existing funds, but it has since determined that might not be feasible. Although the NEM coins have lost most of their value, recovery may still occur. In early 2021, over 30 individuals were charged with the heist.
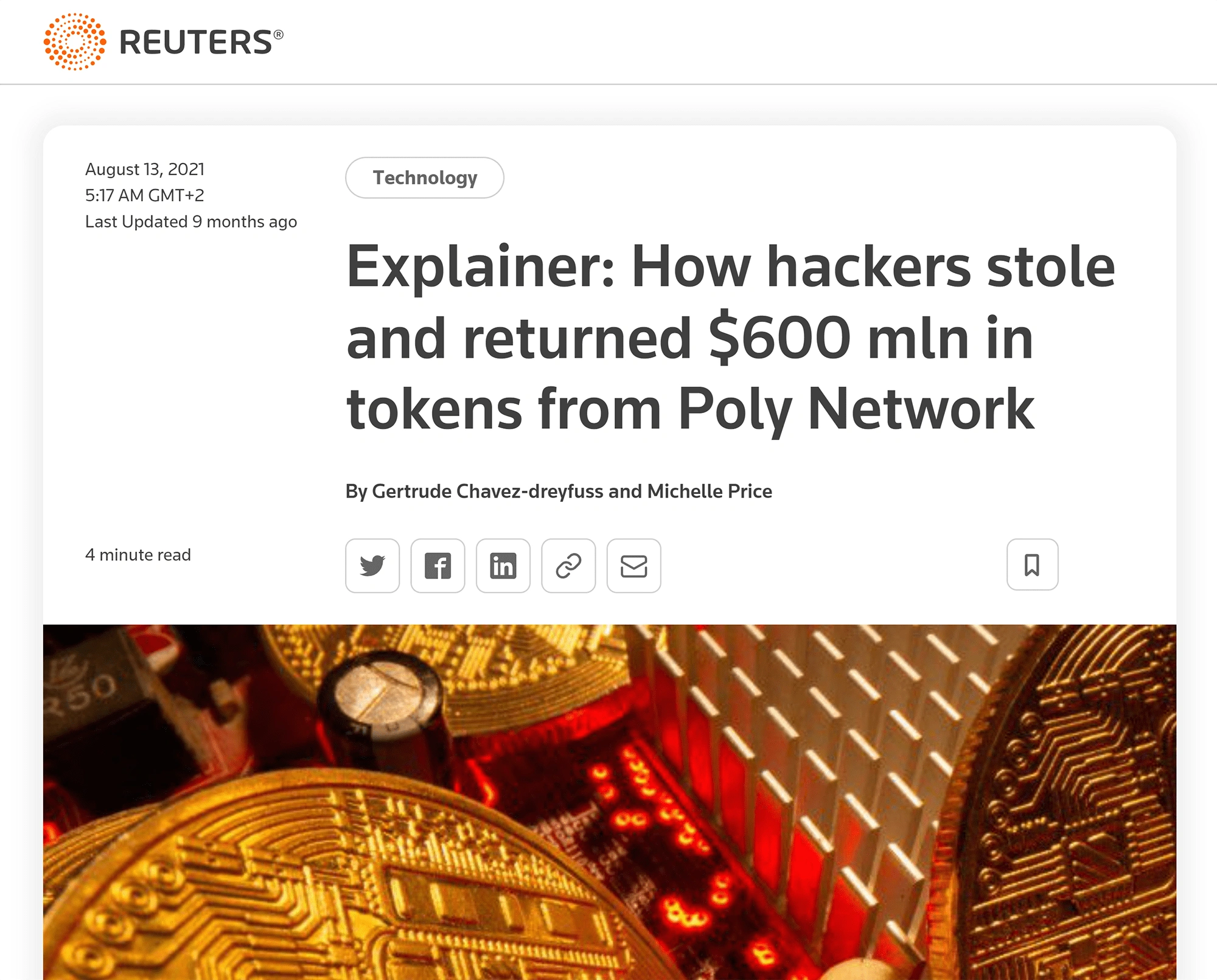
2. Poly Network - $610 Million
Year: 2021
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 260B tokens from USDC, WBTC, DAI, UNI, SHIB, renBTC, USDT, WETH, FEI, ETH, BTCB, BUSD, and BNB
Recovered? Yes
Background:
Poly Network is a DeFi platform that makes it possible to connect different peer-to-peer dApps. Using smart contracts, Poly Network helps to facilitate cryptocurrency transactions between blockchain platforms like Bitcoin and Ethereum. As with other blockchain bridges, the process of using smart contracts to transfer or trade cryptocurrencies across multiple dApps is wrought with vulnerabilities.
The Poly Network has to maintain a high amount of liquidity to cover the transfer of tokens between blockchains. When the hacker noticed a glitch between contract calls in the Poly Network bridge, they could override the contract instructions, diverting funds from the liquidity pool to three different wallet addresses to store the stolen funds.
The hacker claims to have stolen the $610 Million worth of funds to keep Poly Network safe by moving them into a trusted account in an attempt to demonstrate the bug and its potential to cause harm. The hacker’s identity has not yet been discovered. Surprisingly, the hacker - whom the platform referred to as “Mr. White Hat” - returned all the funds stolen a few weeks later.
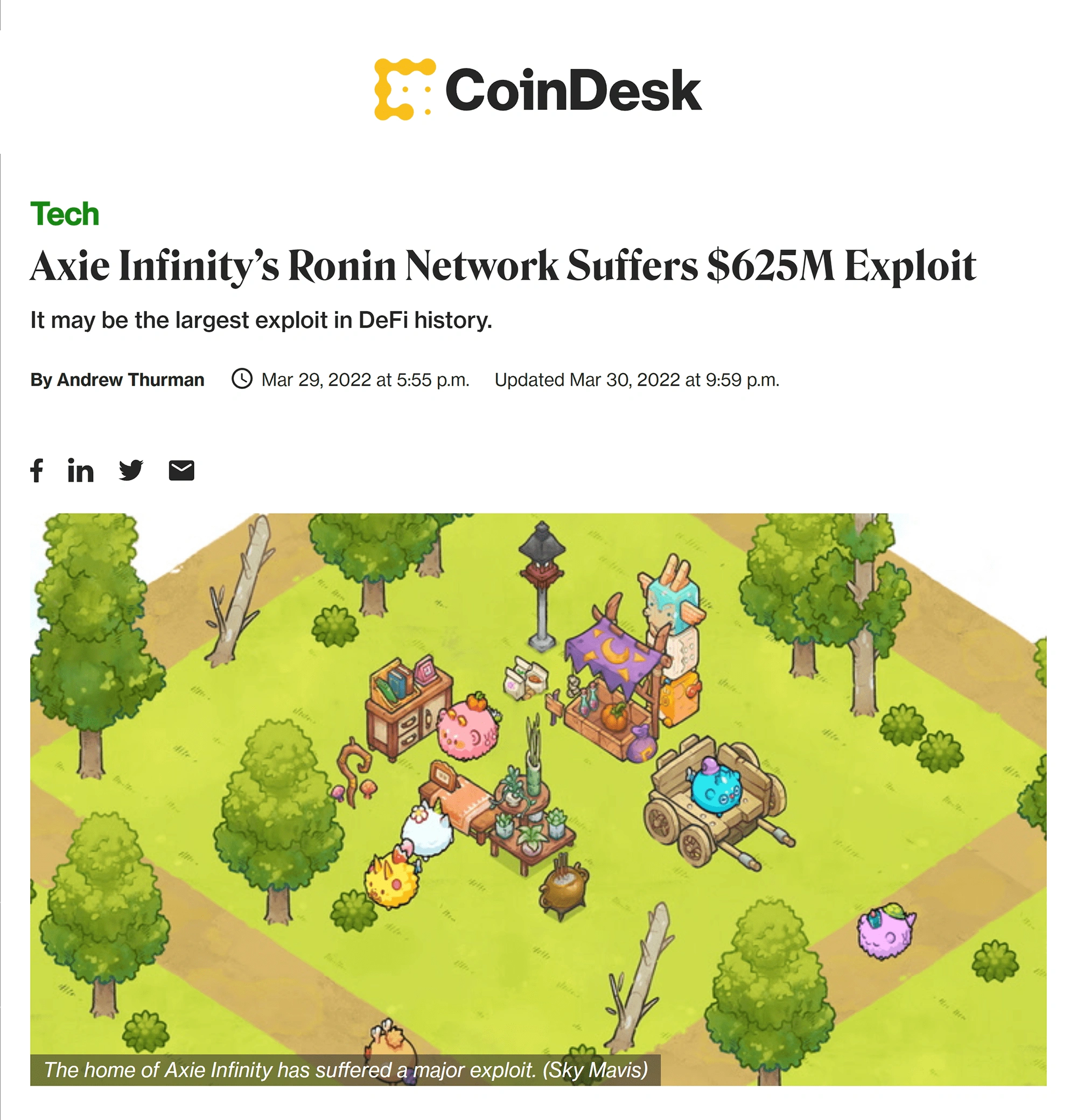
1. Ronin Network (Axie Infinity) - $620 Million
Year: 2021
Type of Heist: Hacker exploitation of system vulnerability
What Was Stolen: 173.6K ETH and $25.5M in USD
Recovered? No
Background:
The Ronin Network is an Ethereum-based "sidechain" (a separate blockchain that runs independently to process transactions.) Sky Mavis explicitly developed Ronin for Axie Infinity - the world’s largest play-to-earn gaming platform - to process transactions on its portal. Touting security and scalability in its whitepaper, with layers of validators on the network, its potential to transform NFTs and gaming platforms looked promising.
A few months after its release, hackers took advantage of the network’s poor security oversight and what seemed like pure negligence. Then, they entered the ring with Conor McGregor's swagger, took control of the RPC node and private keys, and approved two simple transactions by forging fake withdrawals from its bridge contract.
Users were temporarily suspended from withdrawing or depositing funds, but the site and that of its partners were fully restored a few weeks later. Around $5.8M has been recovered so far, and the network has raised $150M to reimburse stolen funds.
Conclusion
If you are unfamiliar with the cryptocurrency world, it can seem like a risky investment. President Biden recently signed an executive order to investigate it, but the cryptocurrency world is still unregulated. As the 2022 FTX scandal proved, without standards and a governing body, it can be challenging to protect investments from thieves on these new blockchain platforms.
And at the rate of new ecosystems popping up, anyone can fall victim to a crypto heist from a network that has rushed their product to market without securing their smart contract vulnerabilities. Smart contracts in blockchain technology can be secure and resistant to attacks when implemented correctly. However, hacks and scams will, unfortunately, continue to happen.
Stop Guessing, Start Growing 🚀
Use real-time topic data to create content that resonates and brings results.
Exploding Topics is owned by Semrush. Our mission is to provide accurate data and expert insights on emerging trends. Unless otherwise noted, this page’s content was written by either an employee or a paid contractor of Semrush Inc.
Share
Newsletter Signup
By clicking “Subscribe” you agree to Semrush Privacy Policy and consent to Semrush using your contact data for newsletter purposes
Written By


Josh is the Co-Founder and CTO of Exploding Topics. Josh has led Exploding Topics product development from the first line of co... Read more