Get Advanced Insights on Any Topic
Discover Trends 12+ Months Before Everyone Else
How We Find Trends Before They Take Off
Exploding Topics’ advanced algorithm monitors millions of unstructured data points to spot trends early on.
Keyword Research
Performance Tracking
Competitor Intelligence
Fix Your Site’s SEO Issues in 30 Seconds
Find technical issues blocking search visibility. Get prioritized, actionable fixes in seconds.
Powered by data from
8 Top Cybersecurity Industry Trends (2024)
You may also like:
Cybersecurity is constantly changing.
While it’s not a new field anymore, new businesses, software, and devices are demanding new levels of data protection. And in some cases, completely new approaches.
We outline the current and future noteworthy cybersecurity trends below.
1. IoT Creates New Cybersecurity Threats
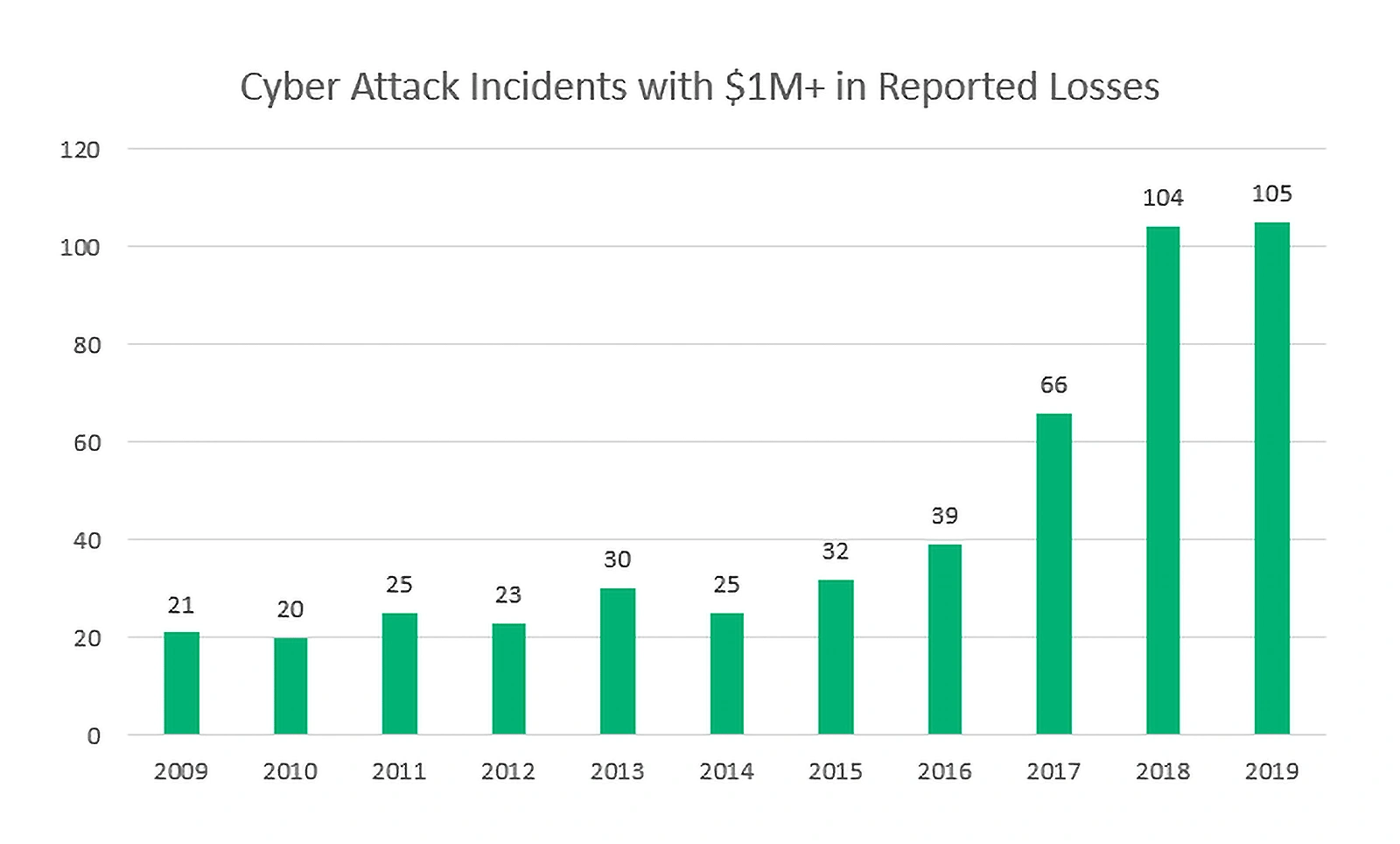
A sharp increase in the development of new technologies and devices is among the biggest reasons for the rise in cyberattacks over the last decade.
Source: Infosec Insights
The Internet of Things (IoT) refers to the billions of physical devices around the globe that collect and share data via the internet. IDC, an international tech analyst company, predicts that more than 41 billion IoT devices will be connected by 2025.
With so many devices thrown into circulation, the opportunity for cyberattacks is expanding at rates that are hard for security companies to keep up.
According to a report by f-secure, the number of cyberattacks recorded in the first half of 2019 was 12 times higher than the previous year, an increase that they credit to the rise in IoT devices.
Source: F-Secure
Everything from fitness watches to baby monitors is at an increased security risk, leaving designers and manufacturers scrambling to enhance security.
According to two surveys conducted by Network World, only 7% of companies and manufacturers have a clearly outlined IoT plan, and over 50% are worried about security issues within their devices.
Additionally, research done by the BDO advisory firm suggests that over 25% of manufacturers don’t even have a security policy for vendors or IoT partners.
Google search traffic shows a 217% increase in cybersecurity technology trends since the start of the COVID-19 global pandemic.
2. Targeted Ransomware Attacks
Targeted ransomware is a type of malware designed to hold a victim’s information at ransom in order to extort something of monetary value from them – most often, cryptocurrency.
The tactics involve denying users and system administrators access to individual files or even entire digital networks, followed by a “ransom note” demanding payment to regain access.
According to a report put out by the US government, over 4,000 daily ransomware attacks happen every day.
(Making it the most prominent method of malware to date.)
In fact, Cybercrime Magazine suspects that a targeted ransomware attack will occur every 11 seconds in 2021, not including attacks on individuals.
The largest payout in 2021 for a single targeted ransomware attack was $40 million, with the average request for ransom fees reaching $200,000 in 2020.
While ransomware attacks can happen anywhere, they are more prominent in countries with more access to internet services.
Over 18% of ransomware attacks occur in the United States, making it the country with the most ransomware attacks.
As a rapidly growing threat in the cybersecurity space, industry experts expect targeted ransomware attacks to continue to increase in the coming years.
Approximately 84% of businesses plan to continue remote work at least partially, even after COVID-19 restrictions are eased and lifted - increasing the risk of data exposure.
Cybercrime Magazine projected total targeted ransomware damages to exceed $20 billion in 2021 alone, expanding the need for increased security - especially for small to mid-sized businesses.
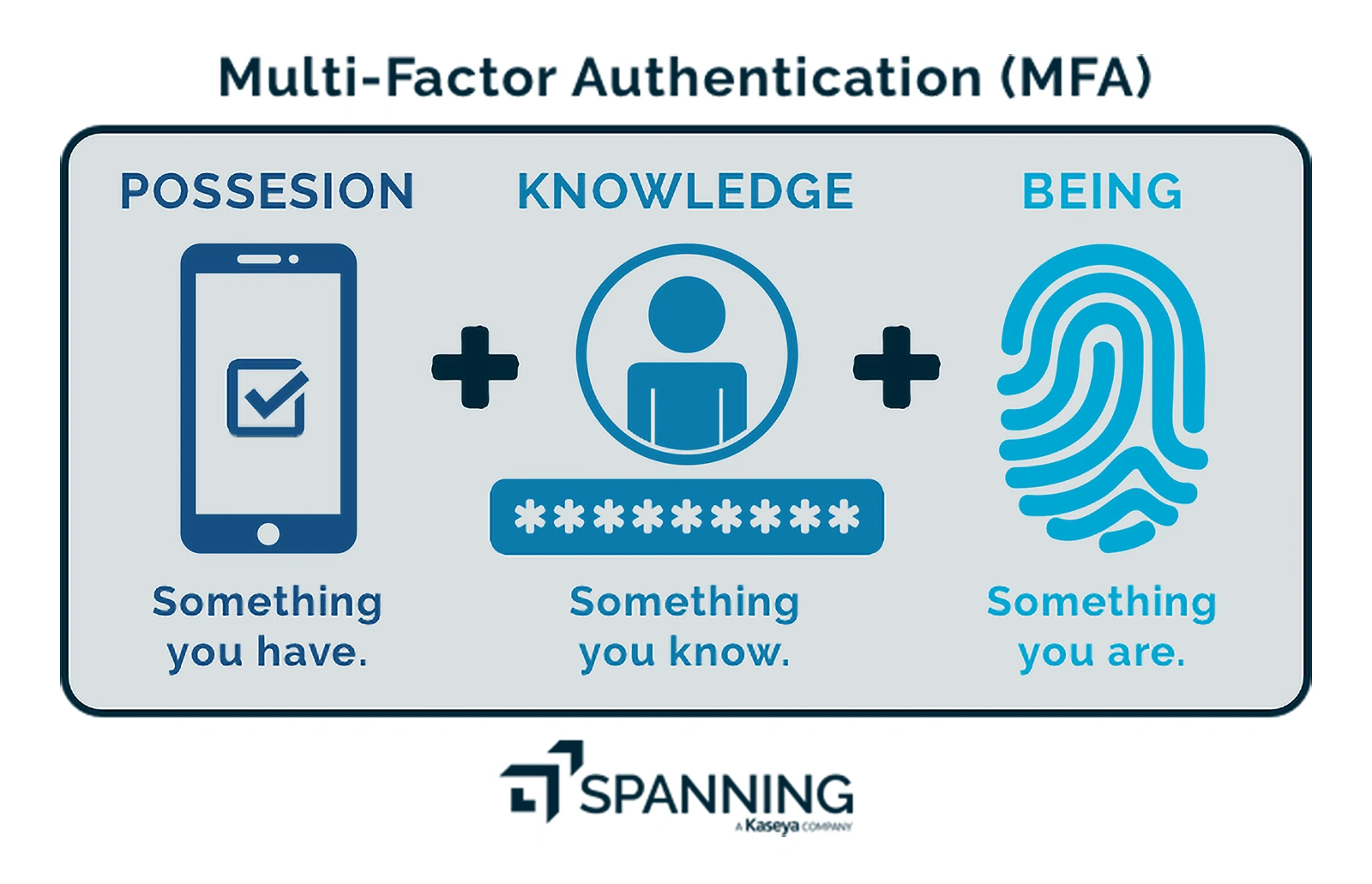
3. Evolution of Multi-Factor Authentication
Source: Spanning
Multi-factor authentication is an electronic authentication method that grants users access to a website or application after submitting two or more types of identity evidence to an authentication system.
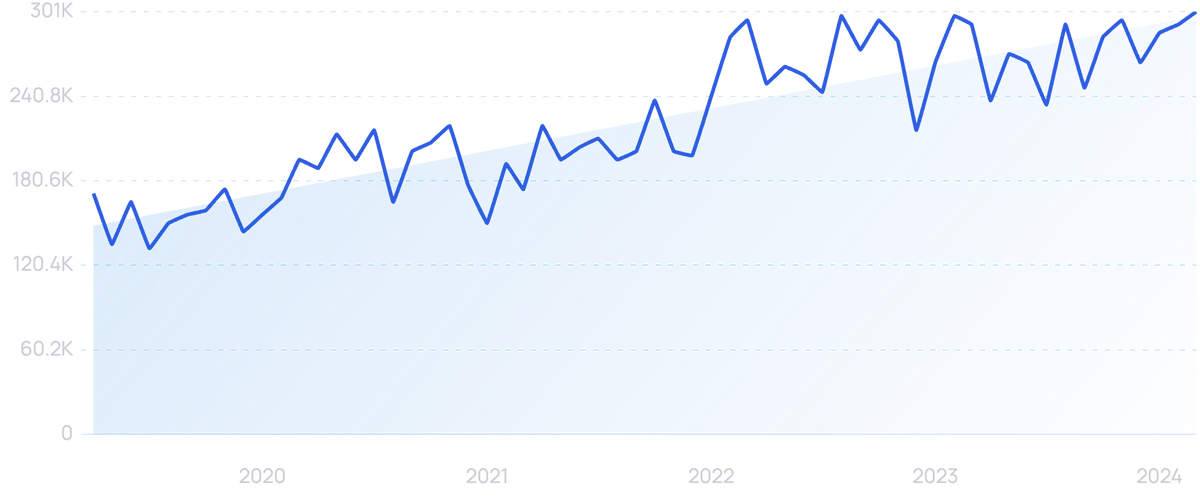
"Multi-factor authentication" receives 301k searches every month.
According to BusinessWire, the multi-factor authentication market was valued at over $10 billion in 2020, with that number expected to surpass $28 billion by 2026.
While most consider multi-factor authentication to be highly secure, companies like Microsoft now urge users to stop using SMS and voice authentication methods due to their increased security risks.
While experts still recommend using SMS authentication if you have no other security options, it is an unencrypted form of messaging.
SMS authentication methods remain vulnerable to automated “man in the middle” attacks.
Online banking is at the highest risk of inefficient multi-factor authentication methods, nearly always done through SMS verification.
To reduce the risk of unauthorized access to accounts, cybersecurity experts are increasingly recommending hardware security keys for verification when possible.
4. Increased Attacks on Cloud-Based Services
Cloud-based services remain at the top of the list of vulnerable cybersecurity risks.
While Google search traffic only shows a 203% trend increase, the rapid adoption of remote work pushes companies to rely more on these cloud-based technologies to communicate and collaborate.
The most costly issues with cloud-based security occur when users misconfigure cloud settings, making way for data breaches, unauthorized access to the network, insecure interfaces, and account takeover.
According to Security Today, the average cost of a data breach amounts to over $3.5 million.
Which makes it imperative for companies to manage and minimize potential cloud-based security threats.
The US and Canada are targeted most often, with losses totaling $7.91 million and $4.74 million, respectively.
According to a recent cloud security report, 68% of companies consider the misconfiguration of assets to be among the most significant contributors to cloud-based security risks.
Further, 75% of companies are either concerned or very concerned about their cloud security and the threats that lie within.
According to a report published by Veronis, cloud-based cyberattacks rose by nearly 630% between January and April last year.
Further, it is estimated that 20% of organizations’ data breaches were caused by remote workers using company cloud-based platforms.
This leads us to our next cybersecurity trend.
5. New Tools to Combat Remote Work Vulnerability
As COVID-19 continues to develop worldwide, many companies are opting to allow their employees to continue to work from home.
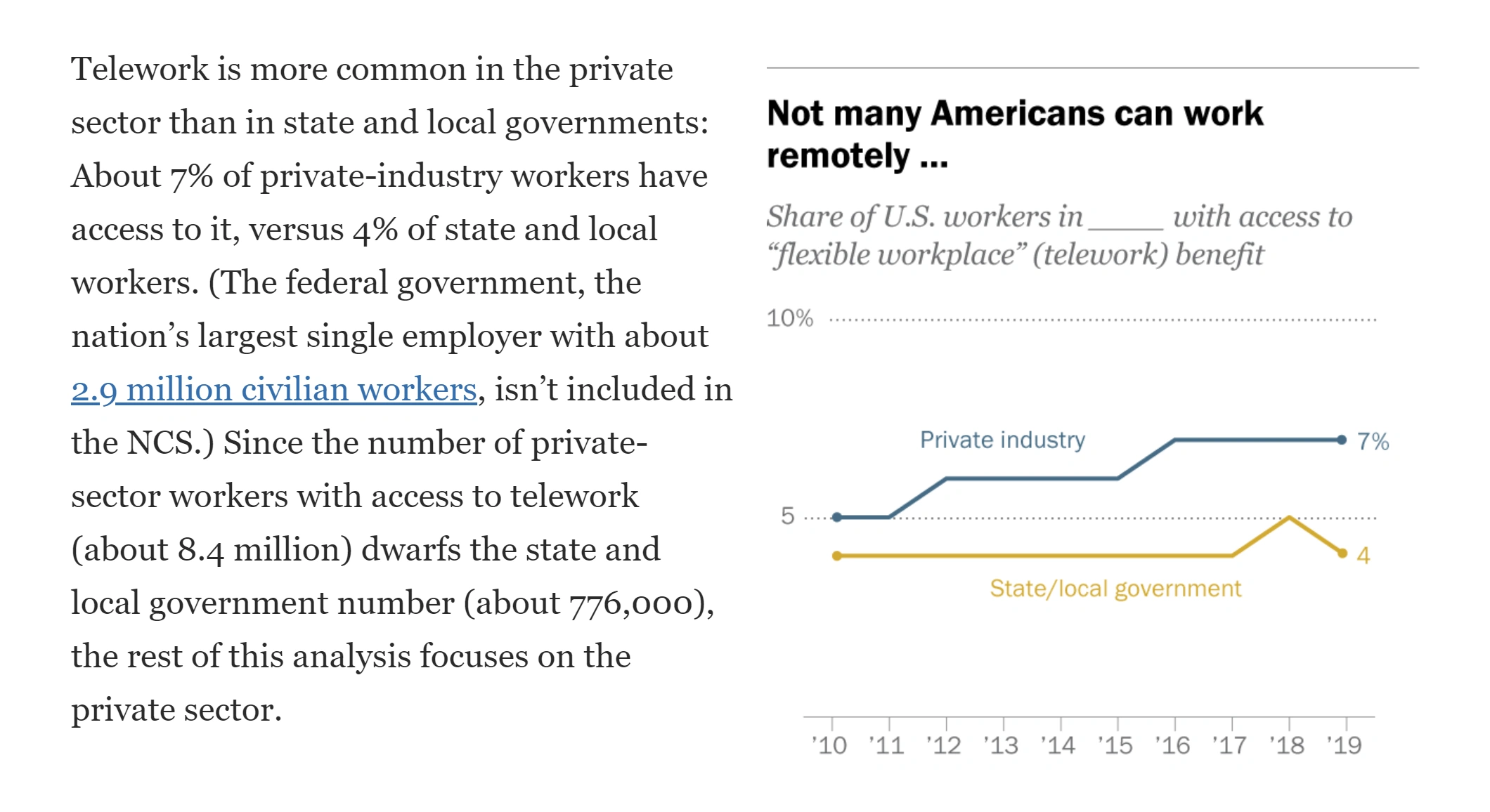
Before the pandemic, only about 7% of private business employees had the option to telecommute.
Source: Pew Research Center
According to a report published by Upwork, over 35 million Americans will be working remotely by the end of 2025 – an 87% increase compared to pre-pandemic statistics.
With the growing use of in-home networks and devices linked to corporate platforms, cybercriminals are increasingly breaching critical corporate systems and services.
In fact, HP reports a 238% rise in global cyberattacks since the beginning of the pandemic.
Organizations that commit to Identity and Access Management Tools (IAM) may reduce risk and better manage their operations.
IAM solutions analyze user activity, streamline safe sign-in procedures based on corporate connective habits, and prompt users for additional authentication when necessary.
6. Organizations Invest In Real-Time Data Monitoring
Real-time data monitoring is a continuously updated stream of data that is used to protect an organization’s IT environment from cyberattacks - most often, cloud-based technology.
Through real-time data monitoring, IT and security professionals can act on data breaches quickly, reducing the risk of monetary loss.
Further, organizations can track and catalog data over long periods, helping to identify system and application behavior anomalies when they occur.
This method of data monitoring is known as “trend monitoring.”
According to a Deloitte review, up to 70% of all data breaches are detected by third-party software instead of an organization’s security team.
Analyst firm IDC estimated that spending in the cybersecurity software market would continue to increase by nearly 9% annually, and spending was predicted to exceed $133 billion in 2022.
They also estimate that enterprises spend over $21 billion on security service providers each year, ensuring round-the-clock data monitoring to reduce and prevent cyberattacks.
7. More Social Engineering Attacks
Social Engineering Attacks describe a wide variety of malicious human interactions. Perpetrators manipulate users into making security mistakes by giving away sensitive information that can lead to financial risk.
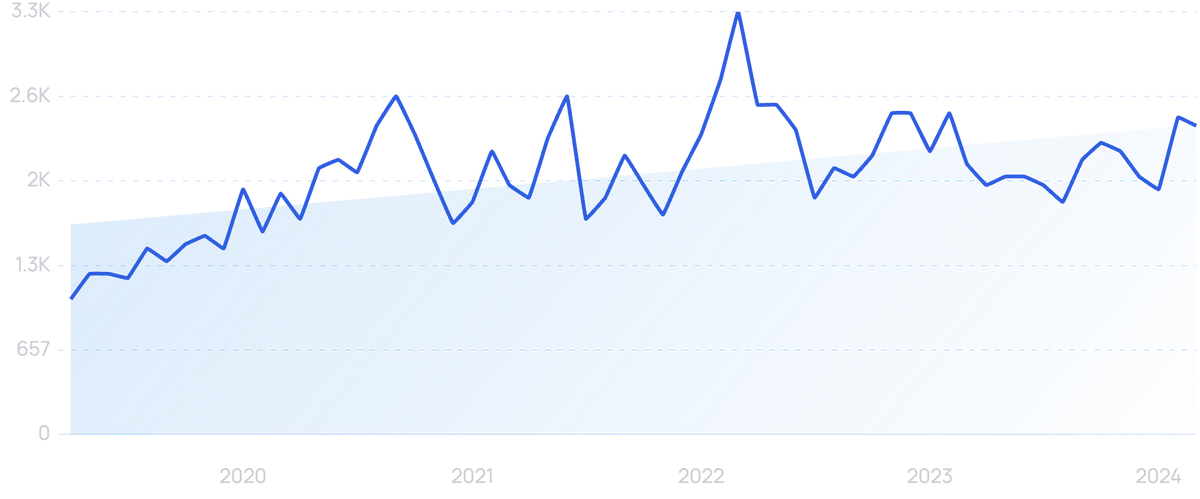
Searches for "social engineering attack" have increased by 213% in 5 years.
Social engineering attacks are dangerous because they rely on human error instead of vulnerable gaps in software and security systems.
This makes them much less predictable than technology-based cyberattacks. And opens up a new avenue for data breaches.
Social engineering takes many forms, with potential attacks occurring anywhere human connections happen.
The following are the five most common types of social engineering attacks:
- Baiting
- Quid Pro Quo
- Phishing
- Pretexting
- Tailgating
Baiting
The most common way of baiting is by dispersing malware through physical forms of media. Attackers might leave something like malware-infected flash drives in areas where victims will likely see them. Once the victim inserts the flash drive into a device, the malware installs on the system.
Quid Pro Quo
Like baiting, quid pro quo social engineering attacks involve a hacker’s request for data or login information in exchange for compensation or service. Commonly, a perpetrator will call the victim and pose as a tech expert with an offer to upgrade a system in exchange for login credentials.
Phishing
Phishing is a technique that uses an automated platform to deliver digital messages to create a sense of urgency so that users give access to vulnerable information.
Phishing is the most prominent form of social engineering attack. According to Verizon, 22% of all data breaches involve phishing.
Pretexting
Pretexting is the human equivalent of phishing, and it is often the first phase in a larger, more grand scheme to access a victim’s information.
Tailgating
Tailgating is used to trick employees into gaining physical access to a company’s premises. Once the attacker is in the restricted area, they use electronic software devices to breach a network and mine valuable data.
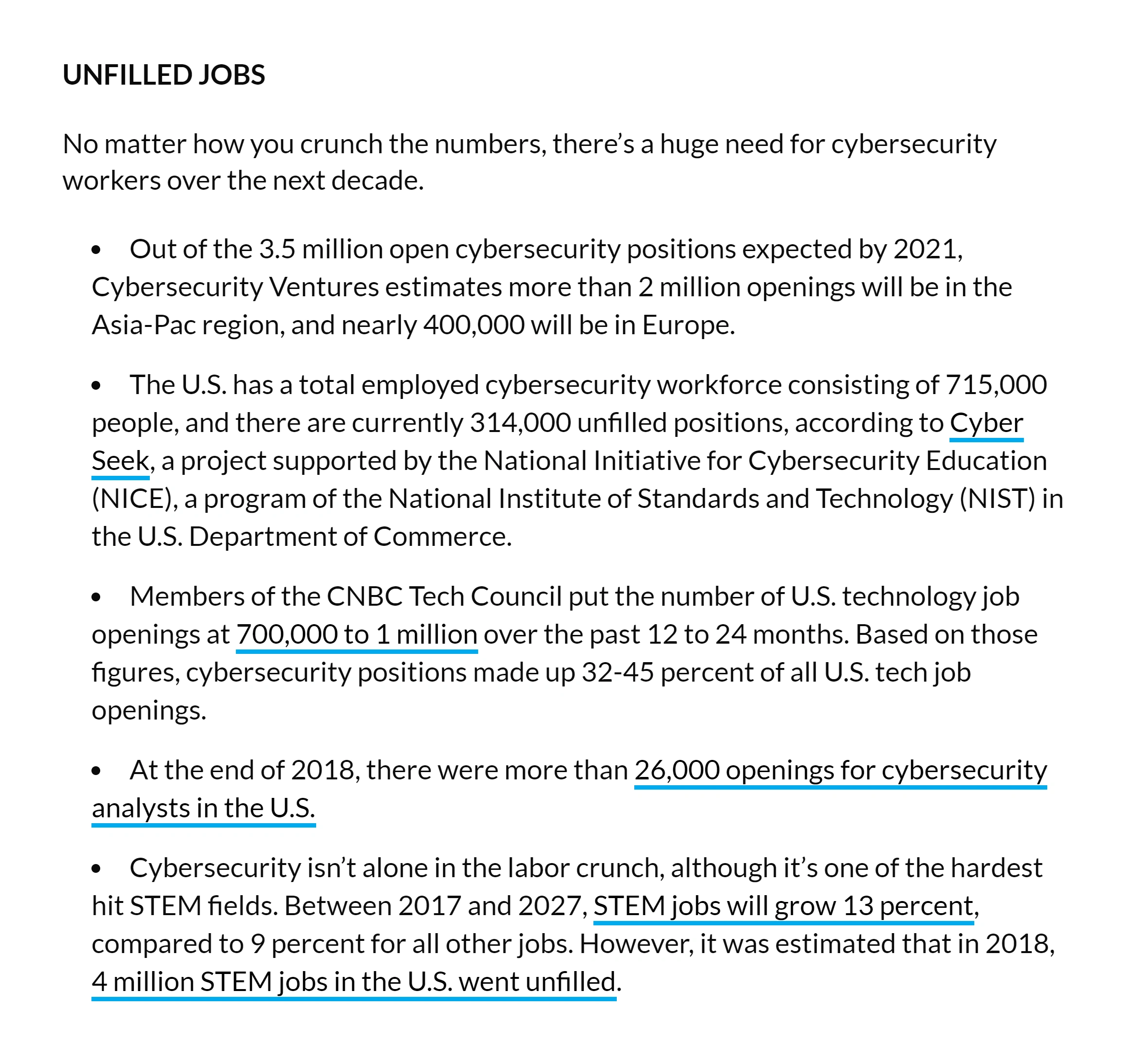
8. Increased Demand for Cybersecurity Professionals
The growing demand for cybersecurity professionals is the overlapping trend for all sections discussed previously and for good reason.
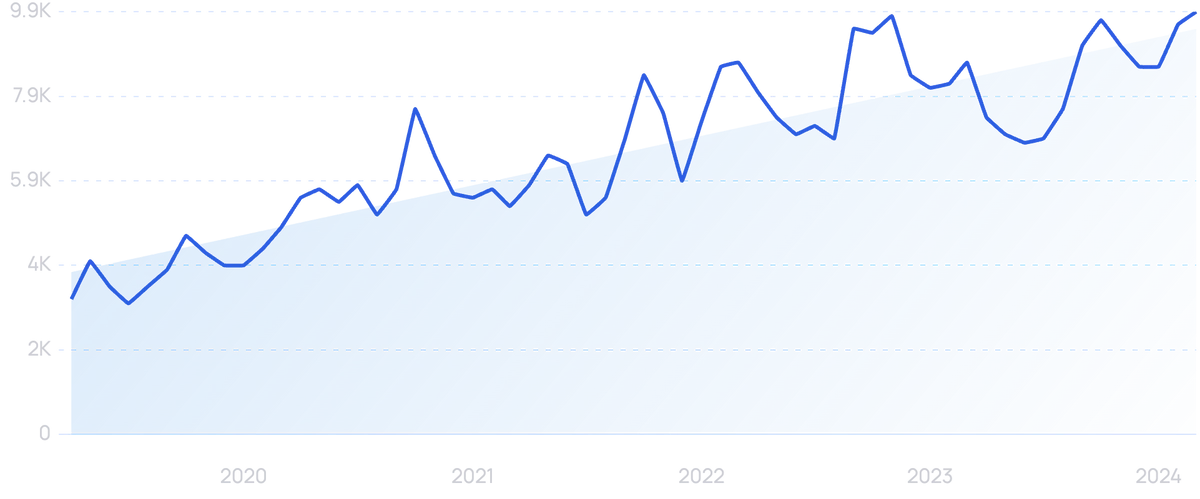
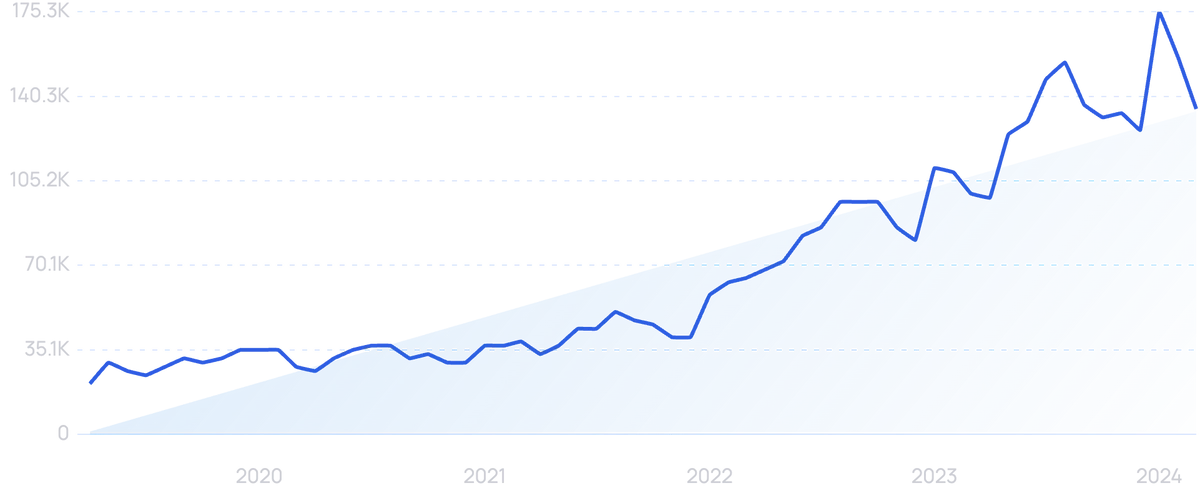
According to Google search data, the market for cybersecurity jobs has seen an increase of over 542% over 5 years.
The Bureau of Labor Statistics estimates that the cybersecurity industry will grow by over 30% throughout the next decade, making it the fastest-growing industry in the US.
Some estimates even suggested that the global cybersecurity workforce would have over 3.5 million vacancies by the end of 2021.
Source: Cybersecurity Ventures
As shown in a report published by the Harvard Business Review, business owners and organizations worldwide realize and understand the looming threat of inefficient cybersecurity.
The report states that most Chief Security Officers are worried about the cybersecurity skills gap. And nearly 60% of interviewed individuals believe the problem will worsen before it gets better.
With a high demand for skilled cybersecurity jobs comes a high earning potential, with the average pay of an Information Security Analyst reaching just over $100,000 a year.
Positions like cybersecurity engineers surpass that mark by huge margins, with salaries ranging from $120,000 to $200,000 per year.
Global cybersecurity losses were predicted to have exceeded $6 trillion at the end of 2021 – it’s no wonder why this field is increasingly lucrative for those who stay relevant.
Conclusion
From cloud-based services to new IoT devices, the technology world is rapidly changing – causing businesses and individuals to change the way they handle cybersecurity.
While we can continue to expect changes in how we handle cyberattacks, the trends above will be of top priority for businesses and governments in 2024.
For more similar content, check out The Ultimate List of Cybersecurity Statistics, Top 20 Cybersecurity Startups to Watch, and Top 25 Cybersecurity Newsletters.
Stop Guessing, Start Growing 🚀
Use real-time topic data to create content that resonates and brings results.
Exploding Topics is owned by Semrush. Our mission is to provide accurate data and expert insights on emerging trends. Unless otherwise noted, this page’s content was written by either an employee or a paid contractor of Semrush Inc.
Share
Newsletter Signup
By clicking “Subscribe” you agree to Semrush Privacy Policy and consent to Semrush using your contact data for newsletter purposes
Written By


Josh is the Co-Founder and CTO of Exploding Topics. Josh has led Exploding Topics product development from the first line of co... Read more